Working on daily tasks with firewalls can sometimes end in a situation where you end up blocking access to the management of your firewall.
This situation is very challenging, regardless of the vendor you are working with.
The end result of this scenario is that you are unable to access the firewall management to remove the rules that are blocking you from reaching the firewall management!
How it’s related to NSX?
Think of a situation where you deploy a distributed firewall into each of your ESX hosts in a cluster, including the management cluster where you have your virtual center located.
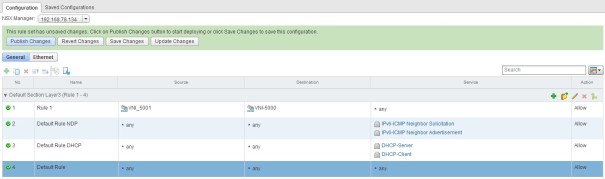
And then you deploy a firewall rule like the one below.
Let me show you an example of what you’ve done by implementing this rule:
Like the poor guy above blocking himself from his tree, by implementing this rule, you have blocked yourself from managing your vCenter.
How we can we protect ourselves from this situation?
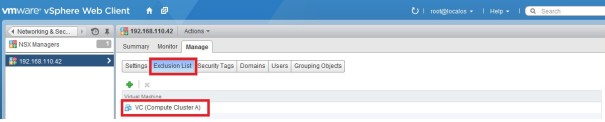
Put your vCenter (and other critical virtual machines) in an exclusion list.
Any VM on that list will not receive any distributed firewall rules.
Go to the Network & security tab Click on NSX Manager
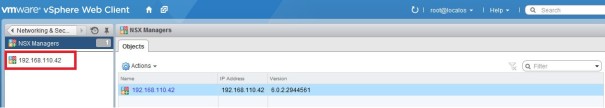
Double click on the IP address object. In my example it is 192.168.110.42
Click on Manage:
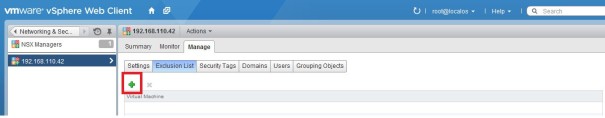
Click on the green plus button.
Choose your virtual machine.
That’s it! Now your VC is excluded from any enforced firewall rules.
What if we made a mistake and do not yet have access to the VC?
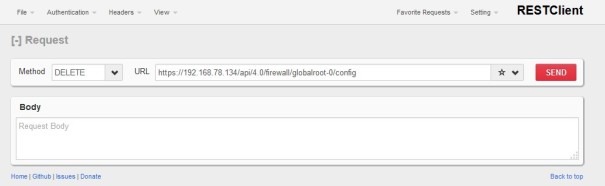
We can use the NSX Manager REST API to revert to the default firewall ruleset.
By default the NSX Manager is automatically excluded from DFW.
Using a REST Client or cURL:
https://addons.mozilla.org/en-US/firefox/addon/restclient
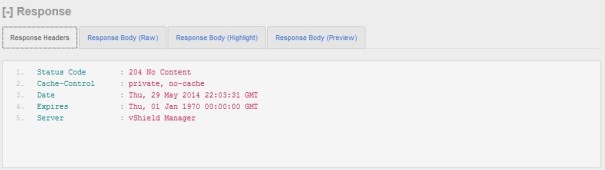
Submit a DELETE request to:
https://$nsxmgr/api/4.0/firewall/globalroot-0/config
After receiving code status 204 we will revert to default DFW policy with default rule to allow.
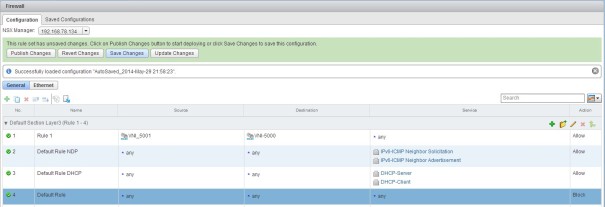
Now we can access our VC, As we can see we revert to default policy, but don’t panic 🙂 , we have saved policy.
Click on the “Load Saved Configuration” button.
Load Saved Configuration before the last Saved.
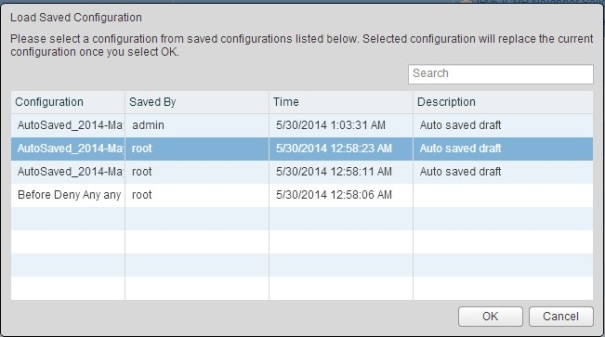
Accept the warning by click Yes.
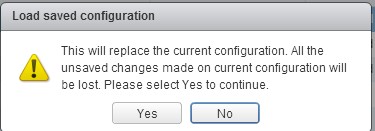
Now we have our last policy before we blocked our VC.
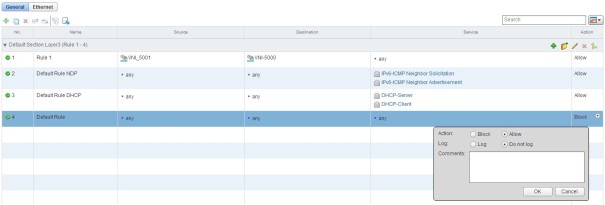
We will need to change the last Rule from Block to Allow to fix the problem.
And Click “Publish the Changes”.
Thank to Michael Moor for reviewing this post




so, if we want our nsx management firewalled, then if VC or nsx is firewalled off is there a solution?